Global: BSA Policy Solutions for Building Responsible AI
APR 09, 2024 | GLOBAL
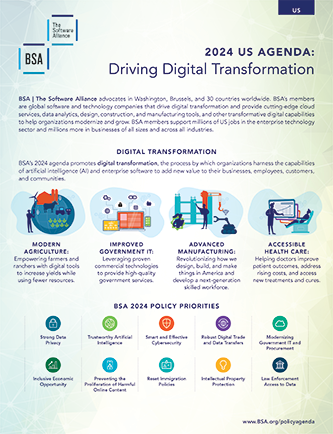
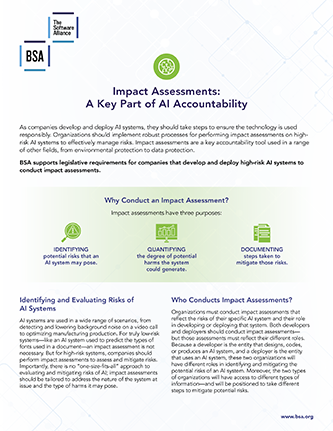
BSA’s Policy Solutions for Building Responsible AI is a comprehensive set of recommendations for policymakers worldwide to address the most artificial intelligence (AI) policy issues and advance the adoption of responsible AI across the economy.
LIRE LA SUITE